The short answer is… nothing. In simple terms, a “Cyber Range,” is part of a multi-layered approach to cyber security, with a heavy emphasis on the greatest cyber threat to SMBs… employees.
That’s right, the biggest cyber breaches are caused by good employees who simply make mistakes because they are not aware of the most common threats. Most employees lack ongoing training. And a once-and-done approach doesn’t work because threats aren’t static, they are forever evolving in today’s cyber landscape.
This is where the “range” comes into play. Cyber threats can be introduced in a multitude of ways. (More on that soon.) The best way to imagine cyber range training is to picture a SWAT team training on a “range” that introduces different types of threats every time they are in the field.
SWAT team members are repeatedly exposed to a plethora of high-risk situations during training. During these exercises, they learn how to be combat-ready, defensibly nimble, and threat savvy. They take their training seriously because lives are at risk.
Cyber range training is equally important for employees because, without it, businesses are at risk.
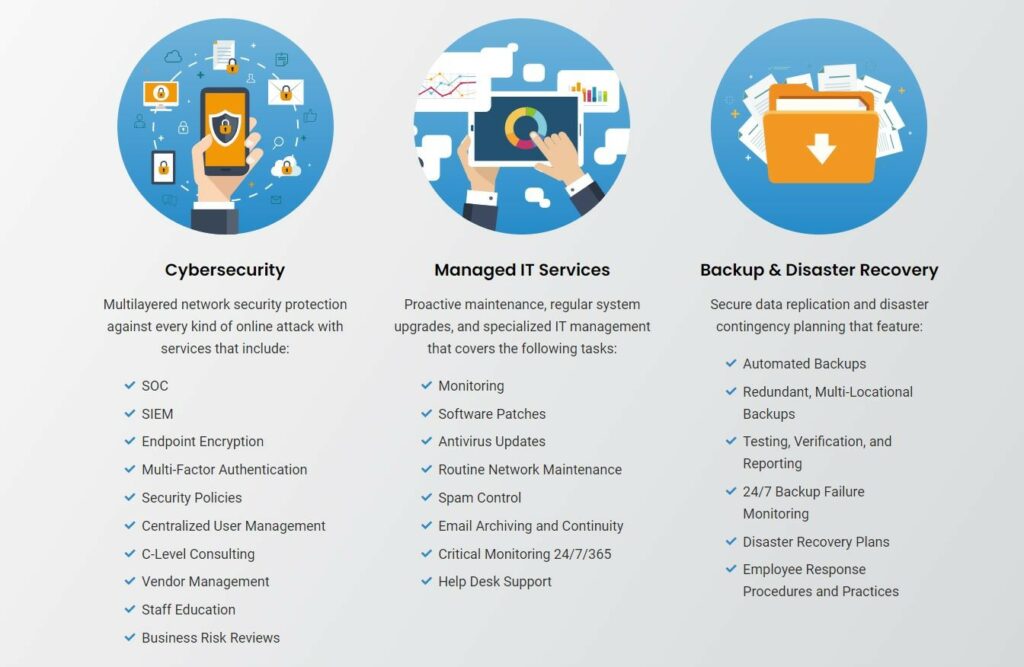
Knowing how important cyber awareness training is, part of Adaptive’s comprehensive cyber security plan includes staff education, employee response procedures, and ongoing training, simulations, and testing – very similar to what is offered in cyber range organizations.
What is a Cyber Range?
According to excerpts from Cybersecurity Guide, they wrote, “A cyber range simulates the worst possible attacks on IT infrastructure, networks, software platforms, and applications. The setup encompasses technology that is able to operationalize and monitor trainee progress and performance as they grow and learn through simulated experiences. When used the right way a cyber range can instill confidence in workers.
The range’s underlying infrastructure might include a network, storage, compute (servers) as well as switches, routers, firewalls, and so forth. The target may consist of “real world” commercial products, e.g., Microsoft Windows Server.
Beyond training, cyber ranges are useful for people and organizations that wish to experiment with new cyber defense technologies. They can use the range as a safe place to solve complex cyber problems. They can test new ideas and see how teams interact with emerging cybersecurity solutions.
Drivers of cyber range development
There are many different drivers of cyber range creation. The real world is not suitable for this kind of training. It is too risky to allow employees to learn cyber skills on production systems and real data. Also, the likelihood of a teachable incident occurring on a schedule that aligns with a training program is extremely low. One could in fact sit around waiting for a major cyberattack for months — but when it comes, it’s essential to be prepared. Hence, the range.
Lack of well-trained cybersecurity professionals
The number one reason cyber ranges are becoming more common and sophisticated is that there are no where near enough trained cybersecurity personnel to meet demand. 82 percent of employers are reporting a deficit of cybersecurity skills among their workforces. Seventy-one percent believe this talent gap is resulting in direct and measurable damage to their organizations.
The growth of highly advanced, constantly evolving attack vectors
As the talent gap grows, the threat landscape becomes all the more serious. Anyone following the news in recent years will have seen a dramatic rise in data breaches and brazen attacks. Almost every corporate and public sector organization is facing attacks. The stakes have never been higher.
A need for training that simulates different kinds of attacks
Attacks are getting more varied and nuanced, too. Professionals need to train on complete technology environments if they want to stand a chance of defending sensitive digital assets from advanced persistent threats (APTs) and other sophisticated attack vectors. These include spear phishing, Distributed Denial of Service (DDoS), bot attacks, API attacks and more. In many cases, detecting the attack requires learning how to spot seemingly minor anomalies in network behavior and device logs. All of this takes intensive training and individual testing to ascertain competency.
A need for readiness
Ultimately, the training and staffing needs, addressed by cyber ranges, are about achieving a high state of readiness for cyber defense. It is not workable to wait until the threat landscape becomes more intense to start training professionals. This must happen now, in alignment with the surging risk occurring in cyberspace worldwide.
Incident response plans need to be tested
Readiness is about more than just filling chairs, however. Being ready to defend digital assets means demonstrating that an operation can respond to incidents. A cyber range provides an environment where professionals can show that they know how to execute incident response plans. This might involve working from established incident response “playbooks” that dictate how to react to various threats.
Different attacks warrant different responses. The way a security operations center (SOC) reacts to a phishing attack will be different from the way it deals with a DDoS, and so forth. On the cyber range, trainees can go through the response processes and attest to their ability to handle a variety of attacks.
The future of cybersecurity ranges
Cybersecurity is becoming more challenging and serious. Organizations, from corporations to state governments, are struggling to find and train the personnel who will enable a robust cyber defense. To remediate this talent gap, they are using cyber ranges to train and test potential employees.
In addition to education and training, cyber ranges play an important role in cybersecurity research and the development of new security products. As the cybersecurity landscape continues to evolve in ever-more threatening ways, the cyber range will have a role to play in preparing professionals to rise to the occasion of cyber defense.”
How an Innovative Cyber Range Helps Companies Prepare for the Inevitable
In a brilliant article by the Globe and Mail, they wrote, “On a Sunday night last December, Toronto’s Hospital for Sick Children (SickKids) declared a “code grey,” a term used to indicate an IT systems failure. The hospital had been hit by a cyberattack, and the criminals responsible were demanding a ransom to restore access. The attack impacted a number of SickKids’ internal clinical and corporate systems, phone lines, and web pages.
While the incident caused delays for lab and imaging results, and affected patient wait times, SickKids later determined that patient care impacts were minimal. This wasn’t luck: Just like any hospital prepares for a healthcare emergency, Sick Kids said it had been preparing for cyberattacks and was able to mobilize quickly.
Still, the cyberattack brought to light a scary reality: No one – not even a hospital full of sick children and their families – is considered off-limits by cybercriminals.
“A common refrain in the cybersecurity industry is, ‘It’s not a matter of if, it’s a matter of when,’” says Trish Dyl, director of corporate training and cyber range, Rogers Cybersecure Catalyst, Toronto Metropolitan University’s national centre for training, innovation, and collaboration in cybersecurity. “However, what many business leaders and executives still don’t understand is that no organization is safe from a cyberattack. So, it is absolutely critical for every organization to defend against and respond to emerging cybersecurity threats.”
The Catalyst Cyber Range is helping organizations do just that, with its unique cybersecurity training and testing platform that provides experiential learning opportunities that are both immersive and ultra-realistic, meaning users are immersed in cyberattack simulations to give them practical, up-to-date training. Catalyst Cyber Range is part of the centre’s comprehensive, experiential cybersecurity training offering designed to strengthen an organization’s cyber posture, or its overall cybersecurity strength and resilience.
“Our experiential training at the Catalyst Cyber Range is about keeping participants on the edge of their seats and helping them pay attention in a different way – not just passively,” Ms. Dyl says. “Our team can assess a company’s response to a cyberattack to find the gaps, with an aim to mitigate negative impacts and lessen the organization’s recovery time.”
Historically, cyber ranges have existed only within large organizations, such as financial institutions or Fortune 500 companies. But today, it’s important that small and medium-sized businesses have access to cyber ranges, because companies of every size can be a target. In fact, nearly half (45 percent) of small businesses in Canada have experienced a random cyberattack in the past year, and 27 percent have gone through a targeted attack, according to a 2022 study by the Canadian Federation of Independent Business (CFIB).
Given the ever-growing need for cybersecurity training, the Catalyst Cyber Range is designed to bring these once-out-of-reach offerings to all organizations. The platform is highly customizable, reflecting the IT environments of the organizations receiving the training, with customized scenarios to reflect the sectors they operate in, whether it’s a ransomware attack at a large hospital or data breach at a small company.
Practice does make perfect when it comes to cybersecurity. According to IBM’s 2022 “Cost of a Data Breach” report, organizations with an incident response (IR) team that regularly tests their IR plan saved an average of US$2.66 million in breach costs compared to those without a plan.
“Practicing the ‘what ifs’ and understanding a cyberattack before it happens is a huge advantage in the learning journey and an important cost-saving exercise,” Ms. Dyl says. “We bring the cyber range concept out of the basement, so to speak, and into the light by offering it to all kinds of organizations. If you invest in the training on an ongoing basis – it’s not one-and-done – it will make a big difference when the time comes to respond.”
Ian McWilliam, an instructor at Georgian College in Barrie, Ont. and a client of the Catalyst Cyber Range, refers to the training as “holistic.” It brings together all the teachings he imparts on his students in one cyberattack simulation, depicting what happens during these events from start to finish.
“When I’m teaching particular areas of cybersecurity, we may focus on that specific silo,” Mr. McWilliam says. “The Catalyst Cyber Range puts it all together. Participants learn about everything that can potentially happen during the attack and defensive measures they can take, and they can monitor what’s happening throughout.”
Being prepared for the inevitable should be a priority, explains Ms. Dyl, and by seeking the right training, organizations can rest assured they have the tools to minimize damage and recover quickly from a cyberattack. “The Catalyst Cyber Range is uniquely designed to show organizations areas they need to improve on, give them the skills to make those changes, and help them be smart about cybersecurity.”
Key Features of Top Cyber Range Solutions
Many times organizations that lack cyber security awareness don’t know where to begin when it comes to training employees. Let’s take a look at excerpts from an article by Aries Security…
“There are quite a few companies who call their products “cyber ranges”. And there are plenty of vendors who will gladly tell you why their product is the best one of them all. But when the sales pitches are over, and the glossy sales sheets are in the recycling bin, it can be challenging to narrow down the key features that separate the real cyber ranges from the posers.
That’s why we’ve put together this quick guide to the top features that we believe set apart a top cyber range solution. In order to make a good decision, being informed is crucial to choosing the right vendor, the right implementation, and the best possible outcome for the organization.
Feature 1: Tools-agnostic
Every environment is different, and every team is different. A good cyber range solution will allow trainees to use the same tools and software during training that they use every day on the job. It’s important to train like you fight; Formula One drivers don’t practice timed laps in their minivans. Why limit your cyber professionals?
Feature 2: Focus on comprehension and competency
The training offered by a cyber range needs to focus on ensuring total comprehension, rather than memorization. Hands-on functional learning is essential: when a real cyberattack strikes, operators must be able to address the threat without relying on an “answer key.” The real world is not like a classroom, and cyber range training must enable trainees to move into practice.
Feature 3: Replay value
Professionals need to maintain their readiness. And in order to do so, they must train in a way that provides functional learning and skills development. Replay value and randomization are key to making sure that trainees can’t simply memorize a set of answers or look them up online in order to progress. An ideal cyber range ensures that no trainee will ever see the exact same question twice. This ensures that mentoring and cross-team learning is possible while still giving students hands-on experience and preventing cheating.
Feature 4: At-a-glance reporting
Cyber range administrators must be able to track training and advancement, provide feedback, and show results. A good cyber range will offer a variety of reporting and metrics tools to provide objective, measurable results. Range reporting should be easy to understand and easy to generate.
Feature 5: Customizable and scalable
All organizations can benefit from cyber range training, but one size does not fit all. A cyber range needs to be customizable and scalable to meet the needs of the customer. Not every implementation will have the same requirements for architecture, security, or clearance level. When choosing a cyber range, ask: how will this scale to our needs? What customizations are possible – or impossible?
Feature 6: Internet connection not required
It may seem counter-intuitive to think of cybersecurity training in an offline environment. But there are many real-world scenarios where this is necessary. For some organizations, security requirements may mandate that certain systems never connect to the corporate network or to the internet. And for deployed military, conferences, and events, there may not be internet access on demand. The ideal cyber range can be used under any circumstances, including without an internet connection.
Feature 7: Easy to set up and deploy
Cyber range training should be easy to use, not create work and make things harder. Look for a cyber range solution that can be deployed efficiently, without requiring additional staff or extensive training. One of Aries’ clients told us that the system needs to be so simple that someone just out of boot camp with limited knowledge can set it up, so admins can do admin work and cyber operators can train. With cybersecurity staff shortages on the rise, having a cyber range that can be run by administrative personnel is a huge time- and labor-saver.
Feature 8: Comes in the format you need
Every organization is different, and every implementation is different. The best cyber range vendors are aware of this and provide products in a variety of formats to suit diverse needs. Whether it’s an offline hardware appliance that allows hardware-in-the-loop, a virtual on-premise solution letting you use your existing infrastructure spend, or a fully cloud-based Software-as-a-Service (SaaS) solution, a cyber range has to come in the format that best fits your organizations needs.”
At Adaptive Office Solutions, cybersecurity is our specialty. We keep cybercrimes at bay by using analysis, forensics, and reverse engineering to prevent malware attempts and patch vulnerability issues. By making an investment in multilayered cybersecurity, you can leverage our expertise to boost your defenses, mitigate risks, and protect your data with next-gen IT security solutions.
Every single device that connects to the internet poses a cyber security threat, including that innocent-looking smartwatch you’re wearing. Adaptive’s wide range of experience and certifications fills the gaps in your business’s IT infrastructure and dramatically increases the effectiveness of your cybersecurity posture.
Using our proactive cybersecurity management, cutting-edge network security tools, and comprehensive business IT solutions, you can lower your costs through systems that are running at their prime, creating greater efficiency and preventing data loss and costly downtime. With Adaptive Office Solutions by your side, we’ll help you navigate the complexities of cybersecurity so you can achieve business success without worrying about online threats.
To schedule a Cyber Security Risk Review, call the Adaptive Office Solutions’ hotline at 506-624-9480 or email us at helpdesk@adaptiveoffice.ca

